To ensure the confidentiality, integrity, and availability of WT information assets, as well as to comply with relevant laws and regulations and mitigate operational risks caused by internal and external threats, an information security policy has been established based on business needs. This policy applies to WT and its subsidiaries that are 100% directly or indirectly owned, controlled, or provide sales and services for the group. It also applies to all personnel within these organizations, including outsourced service providers, interns, and visitors. Information security clauses are incorporated into external contracts accordingly.
Establishing a dedicated department to strengthen information security management
According to the World Economic Forum (WEF) Global Risks Report 2024, “misinformation and disinformation” rank as the number one global risk over the next two years and fifth over the next ten years. The widespread dissemination of false information makes it difficult for individuals and organizations to make accurate decisions and may increase the cost of verifying information. Meanwhile, “cyber insecurity” ranks fourth and eighth over the next two and ten years, respectively. Increasingly complex cyber espionage and cybercrime activities, such as loss of privacy, data fraud, or data theft, pose significant threats. A failure in information security defenses could lead to data breaches and ransomware attacks, or in more severe cases, disruptions to core systems that result in major operational losses and reputational damage.
In view of the growing importance of information security and the proliferation of cyber-attacks, WT Information Security Department is overseen by a Vice-President-level Chief Information Security Officer (CISO). The department is staffed with two dedicated managers and five full-time specialists. Their responsibilities, including security-risk management, incident investigation, vulnerability disclosure, and the assessment and implementation of security architectures, were reported to the Board of Directors on 5 November 2024.
During 2024, no major information security incidents involving the leakage of sensitive data or interruptions to information services occurred, and no financial losses were incurred by customers or suppliers because of security events.
To continually enhance professional capabilities in information security, the company uses the acquisition of security certifications as a performance-review mechanism.In 2024, the team earned four internationally recognized credentials – CCSP, Google CyberSecurity, CEH, and intermediate-level iPAS, covering cloud security, penetration testing, and auditing.In addition to its existing memberships in cooperative defense groups such as the Taiwan CERT/CSIRT Alliance and the Taiwan Chief Information Security Officer Alliance, the company joined the Information Service Industry Association of the R.O.C. (CISA) to share intelligence on security trends and threats, thereby strengthening its joint-defense ecosystem.
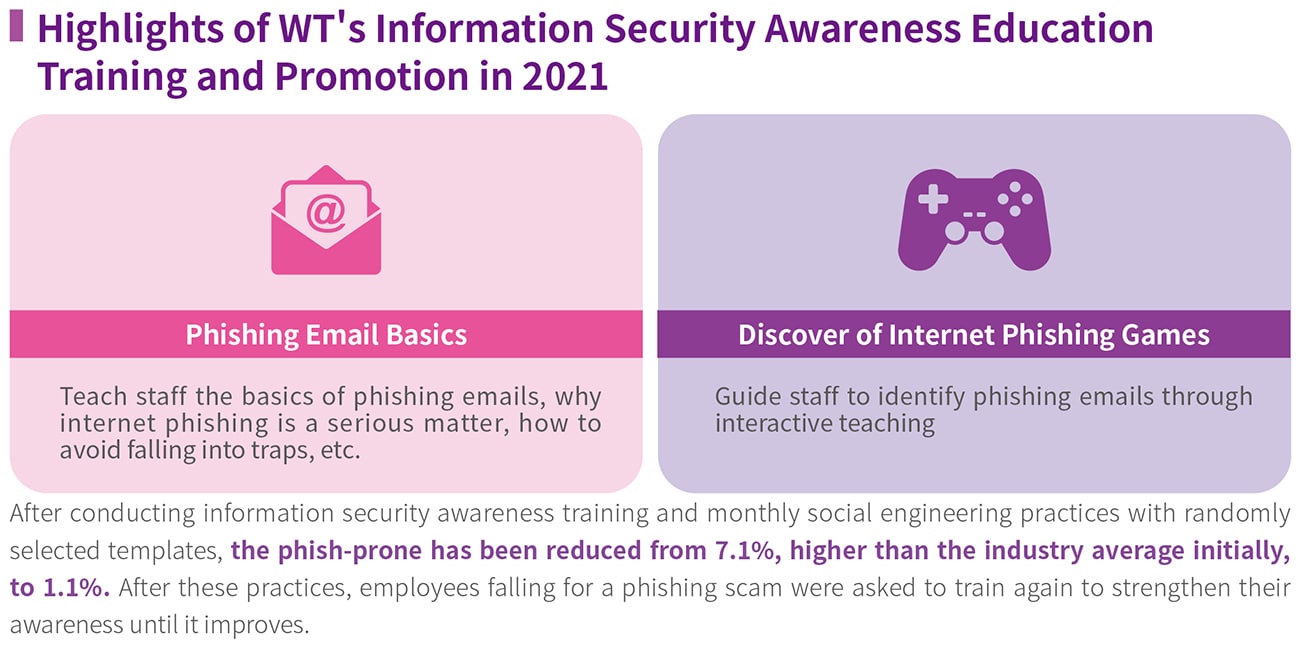
Ongoing enhancement of employee cyber-security awareness
As traditional perimeter defenses lose effectiveness, employee awareness has become pivotal to cyber-security management. Since 2021, WT has conducted monthly social-engineering drills using random phishing templates. Employees who click on suspicious links undergo retraining and their immediate supervisors are notified; results are regularly tracked to reduce awareness-related threats. Beginning in 2024, the scope of our security-awareness training and phishing-simulation exercises was expanded to cover employees from both Excelpoint and Future Electronics.
Strengthening the security framework to build corporate resilience
Guided by ISO 27001 and the NIST Cybersecurity Framework, WT applies defense-in-depth and secure-by-design principles across eight layers: governance, data, endpoints, applications, networks, third-party supply, business continuity & incident response, and threat intelligence & joint defense. Residual risks are continuously monitored. External ISO 27001 audits and red-team exercises validate our controls. WT holds ISO/IEC 27001:2013 and CNS 27001:2014 certificates, valid through 2025. Key 2024 actions mapped to the NIST CSF 2.0 functions are:
Govern
Strengthening cyber-security governance and network protection
WT follows a “defense-in-depth” and “security-by-design” approach. Guided by Continuous Threat Exposure Management (CTEM), we proactively identify assets with vulnerable attack paths and apply risk-management controls to reduce both the likelihood and impact of incidents. Our 2024 cyber-security controls include the following:
• Daily collection and analysis of domestic & international cyber-security news, open-source intelligence (OSINT), and vendor / ISAC advisories.
• Annual third-party penetration tests or red-team exercises.
• Deployment of Endpoint Detection & Response (EDR) on PCs and servers with regular updates and real-time analytics.
• Activation of behavioral-analysis modules and adoption of Managed Detection & Response (MDR) services.
• Encryption of sensitive data in transit and at rest.
• Annual in-house processing of retired information assets to ensure media are unreadable.
• Engagement of external specialists for de-magnetisation and physical destruction of retired assets, followed by disposal at government-accredited recyclers under escorted, fully logged procedures.
• Weekly vulnerability scanning with risk-based patch prioritisation and scheduled patch management.
• Implementation of Multi-Factor Authentication (MFA) and regular weak-password checks per NIST 800-63B.
• Use of FIDO2 hardware keys for critical cloud services to mitigate credential theft and brute-force attacks.
• Deployment of next-generation firewalls (NGFWs) featuring application awareness, Intrusion Prevention (IPS) and Advanced Threat Protection (ATP).
• Identity-aware segmentation that separates employee and visitor access paths.
• Enhanced email security with advanced threat-protection modules to improve content analysis.
Addressing customers’ cyber-security concerns
WT’s transactions throughout the supply chain rely heavily on IT systems and online platforms. Customers and original-equipment suppliers regularly evaluate us through cyber-security self-assessment questionnaires and hold ad-hoc discussions on specific security topics. To meet customer requirements, third-party security service providers engaged by the customers carry out host vulnerability scanning and penetration testing to safeguard supply-chain information security.
| Sources of Cyber-Security Information | |
| 1. Customers | 5. Cyber-security service providers |
| 2. Original-equipment suppliers | 6. Cyber-security news outlets or specialist websites |
| 3. Cyber-security information-sharing alliances / ISACs | 7. Zero-day exploit intelligence and similar alerts |
| 4. IT hardware & software vendors | 8. External risk-management platforms |
Business continuity and emergency response
24/7 cybersecurity monitoring without interruption
WT has established a dedicated cybersecurity email inbox to receive diverse external threat intelligence, using it to reinforce internal safeguards. The company has also entered into managed-service agreements with third-party providers for a Security Operation Center (SOC) and Managed Detection and Response (MDR). This always-on, 24 × 7 mechanism enables continuous, real-time monitoring of cybersecurity threats.
Regular cybersecurity-incident drills to ensure the fastest possible recovery
To strengthen corporate resilience and maintain high availability of information systems, WT carries out at least one test and drill each year under the Cybersecurity Management System’s Business Continuity Plan. The exercise simulates a primary-system failure, switches the main data center to a remote site, records results in detail, and folds lessons learned into continual-improvement tracking.
Between April and June 2024, unplanned power outages increased by roughly 50 % compared with the same period the previous year. WT therefore continues to run power-failure drills that simulate sudden blackouts, ensuring emergency generators start promptly and all facilities and systems remain operational. Post-exercise reviews confirmed that the response procedures are appropriate and that every facility and system functioned normally throughout the test.
Establishing cybersecurity reporting tiered management & rapid response
WT has issued a Security-Incident Management Procedure that defines four severity levels and the associated escalation flow. When an incident occurs, the person who discovers it reports the details or security staff perform an incident determination; notifications are then sent in line with the assigned level. If the incident is classified as “major”, it must be reported immediately to the Chief Information Security Officer (CISO), who in turn briefs the General Manager for follow-up emergency-response management.
The IT department must eliminate and resolve cybersecurity incidents within the target resolution time. After closure, it conducts a post-incident review and implements improvement actions to prevent recurrence. If an incident results from an individual employee’s behavior, the root cause and impact are assessed and disciplinary measures are imposed in accordance with work rules.
In 2024, five cybersecurity incidents occurred. All were classified as non-major and involved credential leakage; each was handled and contained immediately, resulting in no impact. None of the incidents led to any compromise of core services or leakage of sensitive data.
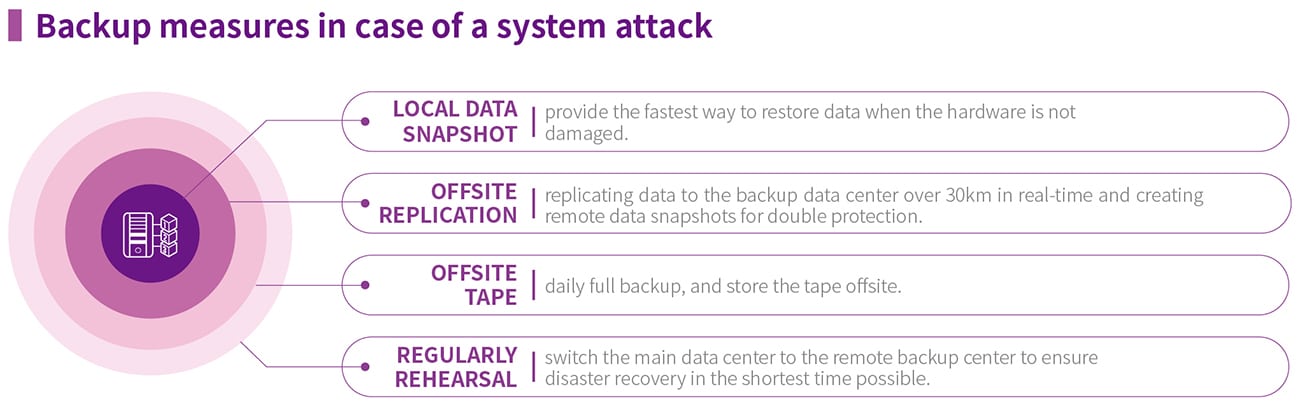
Backup measures when the system is under attack
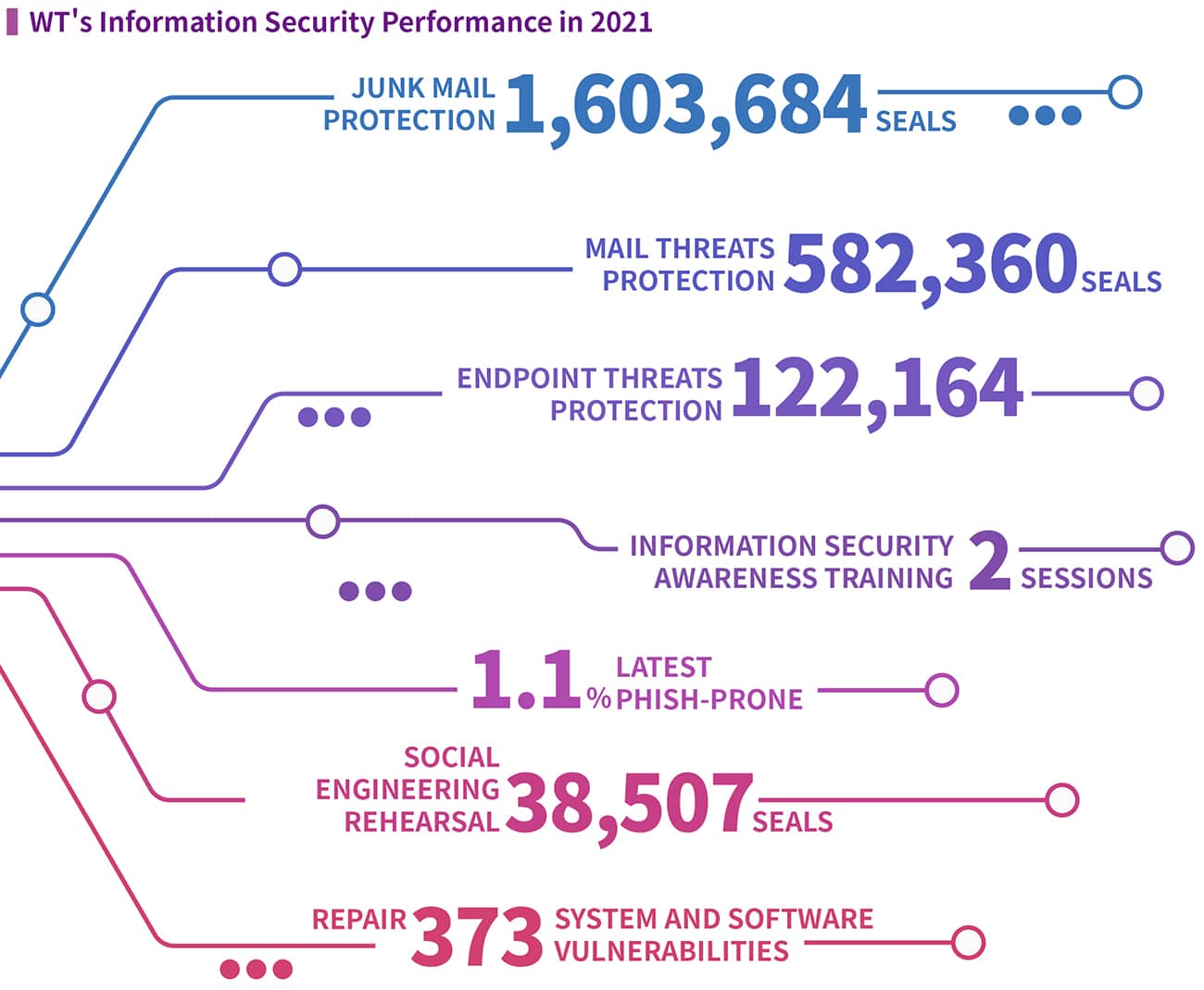
2024 WT’s Cybersecurity Performance
∙ Two rounds of company-wide cybersecurity-awareness training, plus one intensive session for core-system personnel and managers.
∙ Phishing-simulation campaign: 278,037 emails sent; employee click-through rate 0.7%, comfortably below the 5% industry average target.
∙ Blocked 39,553,348 spam emails and shielded against 1,576,611 malicious emails.
∙ Intercepted 28,782 endpoint-threat events.
∙ Patched 134,736 system and software vulnerabilities.
∙ Earned four additional international cybersecurity certifications and logged 200+ hours of professional training.

2025 cybersecurity management plan